
Posted On July 07 2024 | 16:20
1. AI-Powered Phishing Campaign
The digital revolution has transformed the way we communicate, conduct business, and access information. However, this increased connectivity has also exposed us to a growing array of cyber risks, ranging from data breaches and ransomware attacks to sophisticated hacking attempts and state-sponsored cyber espionage. Cybersecurity has become a top priority for organizations of all sizes, as the consequences of a successful cyber-attack can be devastating, both financially and reputationally.
Understanding the evolving landscape of cyber threats
The cybersecurity landscape is constantly evolving, with new threats and vulnerabilities emerging at an unprecedented pace. Cybercriminals are becoming increasingly sophisticated, leveraging advanced technologies and techniques to infiltrate even the most well-protected systems. From phishing scams and malware to distributed denial-of-service (DDoS) attacks and nation-state-backed cyber operations, the range of cyber threats is vast and ever-changing.
To effectively navigate this dynamic landscape, it is essential to stay informed about the latest cyber threats and the strategies used by threat actors. This requires a deep understanding of the threat landscape, including the motivations, tactics, and techniques employed by cybercriminals. By staying vigilant and proactively monitoring for emerging threats, organizations can better prepare themselves to detect, respond to, and mitigate the impact of cyber-attacks.
Get in touch with People Tech Group to know more about our cybersecurity services.
The role of transparency in cybersecurity
In the face of these evolving cyber threats, transparency has emerged as a critical component of effective cybersecurity. The traditional approach of keeping cybersecurity strategies and incident response plans under lock and key is no longer tenable. Instead, a culture of transparency and information-sharing has become crucial for enhancing the overall security posture of organizations and the broader cybersecurity ecosystem.
Transparency in cybersecurity involves openly sharing information about cyber threats, vulnerabilities, and best practices. This includes disclosing data breaches, reporting on cyber incidents, and collaborating with industry peers, government agencies, and security researchers. By fostering a transparent environment, organizations can learn from each other’s experiences, implement effective countermeasures, and collectively strengthen the defenses against cyber-attacks.
Challenges and opportunities in securing the digital frontier
While the importance of cybersecurity is widely recognized, the task of securing the digital frontier is fraught with challenges. Cybercriminals are constantly evolving their tactics, and the pace of technological change often outpaces the ability of organizations to keep up. Limited budgets, skills shortages, and the increasing complexity of IT infrastructures can further compound the challenges faced by security teams.
However, within these challenges lie significant opportunities for organizations to enhance their cybersecurity posture. By embracing innovative technologies, such as artificial intelligence and machine learning, organizations can automate and streamline their security operations, enabling them to detect and respond to threats more effectively. Additionally, the growing emphasis on cybersecurity education and training can help organizations build a skilled and resilient workforce capable of navigating the evolving cyber landscape.
The role of artificial intelligence and machine learning in cybersecurity
As the cybersecurity landscape continues to evolve, the role of emerging technologies, such as artificial intelligence (AI) and machine learning (ML), has become increasingly crucial. These advanced technologies can revolutionize the way organizations approach cybersecurity by automating and streamlining various security functions, improving threat detection and response, and enhancing overall resilience.
AI and ML-powered security solutions can analyze vast amounts of data, identify patterns, and detect anomalies at a scale and speed that far exceeds human capabilities. This enables organizations to rapidly identify and respond to cyber threats, reducing the time between detection and mitigation. Additionally, these technologies can be used to automate repetitive security tasks, freeing up security teams to focus on more strategic initiatives.
The impact of regulations on cybersecurity practices
Regulatory frameworks and compliance requirements have also become integral to the cybersecurity landscape. Governments and industry bodies have introduced a range of regulations, such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA), to mandate specific security standards and data protection measures.
Compliance with these regulations has become a critical concern for organizations, as the consequences of non-compliance can be severe, including hefty fines and reputational damage. Navigating the complex web of regulatory requirements can be a significant challenge, but it is essential for organizations to understand and adhere to these rules to protect their assets and maintain the trust of their stakeholders.
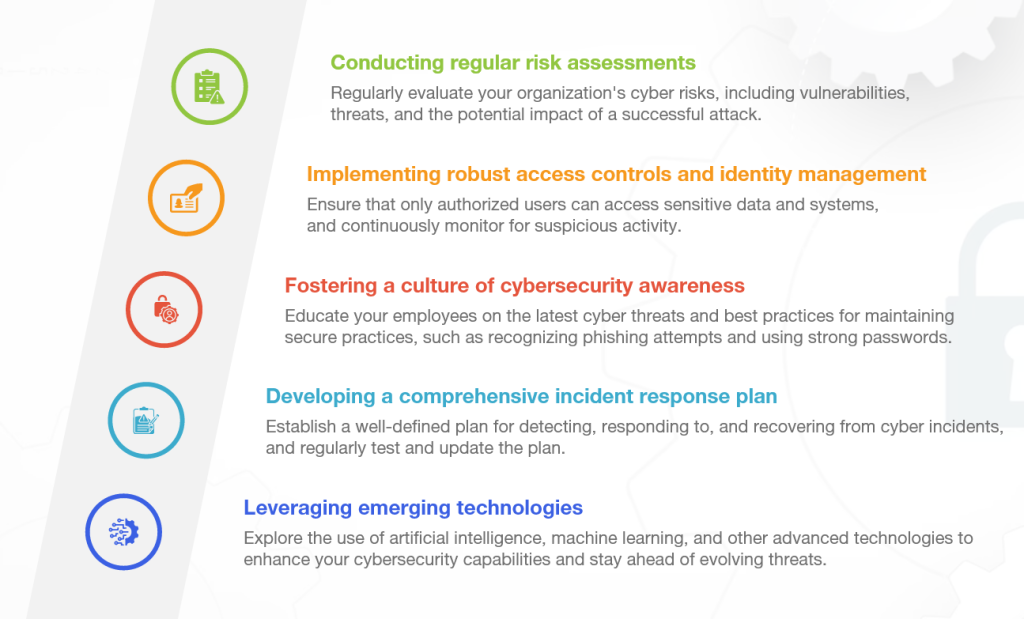
Building a resilient cybersecurity framework for your organization
- Risk assessment and management: Regularly evaluate your organization's cyber risks and implement appropriate mitigation strategies.
- Robust access controls and identity management: Ensure that only authorized users can access sensitive data and systems.
- Comprehensive incident response and business continuity planning: Develop and regularly test your organization's incident response and disaster recovery plans.
- Employee training and awareness: Foster a culture of cybersecurity awareness through ongoing training and education programs.
- Continuous monitoring and threat intelligence: Leverage advanced technologies and security tools to detect, analyze, and respond to cyber threats in real-time.
- Third-party vendor management: Assess and manage the cyber risks posed by your organization's external partners and service providers.
- Increased focus on cloud security: As more organizations migrate their data and operations to the cloud, the demand for robust cloud security solutions will continue to grow.
- Expansion of the Internet of Things (IoT) security: With the proliferation of connected devices, securing the IoT ecosystem will become a top priority for organizations.
- Advancements in artificial intelligence and machine learning: The use of AI and ML in cybersecurity will continue to expand, enabling more proactive and intelligent threat detection and response.
- Heightened emphasis on supply chain security: Securing the complex web of third-party vendors and suppliers will become a critical component of an organization's cybersecurity strategy.
- Increased regulatory scrutiny and compliance requirements: Governments and industry bodies will continue to introduce new regulations and standards to enhance data privacy and security.
Concluding: Embracing the future of cybersecurity
In the ever-evolving digital landscape, the importance of cybersecurity cannot be overstated. As the threats continue to grow in sophistication and complexity, organizations must embrace a comprehensive and proactive approach to securing their digital assets.
By fostering a culture of transparency, leveraging emerging technologies, and building resilient cybersecurity frameworks, you can navigate the future of cybersecurity with confidence. Remember, the digital frontier is a constantly shifting landscape, and the key to success lies in your ability to adapt, innovate, and stay ahead of the curve.
Don’t let your organization become a victim of a cyber-attack. Contact our cybersecurity experts today to learn how we can help you secure your digital frontier and prepare for the future of cybersecurity. Schedule a consultation with our experts or write to us at info@peopletech.com.
